Introduction
In today’s digital age, personal privacy and data security have become increasingly important. With cyberattacks and data breaches on the rise, it is crucial for individuals and businesses alike to protect their sensitive information. One powerful security measure that has gained significant attention is End-to-End Encryption (E2EE). Most of the virtual private network (VPN) solutions seamlessly provide encryption facilities. This groundbreaking technology has revolutionized the way we communicate and ensures that our private conversations and data remain secure from prying eyes.
In this article, we will delve deeper into the world of E2EE and explore its importance in safeguarding our digital lives. So, put on your digital security hats, and let’s unravel the mysteries of End-to-End Encryption.
Table of Contents
What is End-to-End Encryption (E2EE)
End-to-End Encryption (E2EE) is a security measure that ensures the protection of data as it travels between two endpoints. In simple terms, it means that only the sender and recipient can access and read the information being transmitted, with no intervention from any third party, including government agencies or service providers. This method of encryption has gained significant attention in recent years due to concerns over data privacy and security breaches.
How Does it Work?
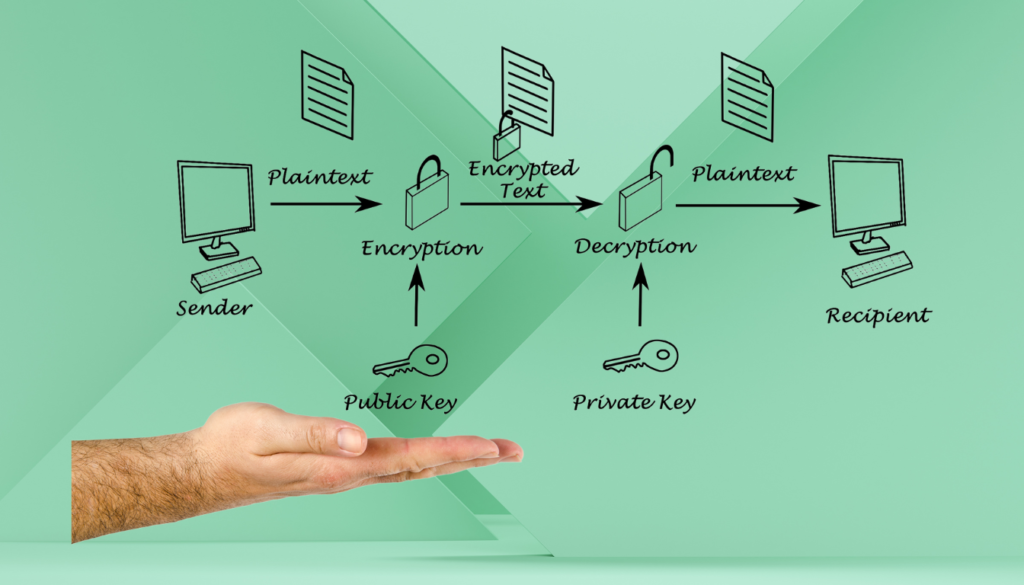
So, how does E2EE work? When a user sends a message, it gets encrypted on their device using a unique encryption key. This encrypted message then travels through various networks and servers to reach the recipient. However, during this journey, the message remains scrambled and unreadable to anyone other than the sender and recipient. Once the message reaches the recipient’s device, it gets decrypted using a matching decryption key, and the original message is revealed.
The beauty of E2EE lies in the fact that the encryption and decryption process occurs exclusively on the users’ devices, without any involvement from the applications or service providers facilitating the communication. This ensures that even if the data is intercepted during transmission or stored on servers, it remains incomprehensible to anyone other than the intended parties. As a result, E2EE provides a powerful defense against unauthorized access and surveillance, giving individuals greater control over their information.
The Benefits of End-to-End Encryption (E2EE)
| Benefit | Description |
|---|---|
| Enhanced Privacy | Ensures that only the communicating users can read the messages, protecting privacy from eavesdroppers. |
| Improved Security | Protects data from potential breaches, making it extremely difficult for hackers to access the encrypted content. |
| Data Integrity | Guarantees that the data sent is the same as the data received, preventing tampering during transmission. |
| User Trust | Builds trust with users by demonstrating a commitment to protecting their data and communications. |
| Compliance with Regulations | Helps organizations comply with privacy laws and regulations, like GDPR, HIPAA, etc., that require data protection. |
| Reduced Risk of Data Breaches | Minimizes the impact of data breaches, as encrypted data is unreadable and useless without the decryption keys. |
| Secure Communications | Ensures that conversations, whether text, voice, or video, are secure and cannot be intercepted. |
| Protection against Surveillance | Shields users from government and corporate surveillance by keeping communications private. |
| Confidentiality in Business | Safeguards sensitive business information and intellectual property from competitors and cyber threats. |
| Long-term Security | Provides a level of security that remains robust even as technology advances and decryption techniques improve. |
Extra Layer of Security
One of the key benefits of E2EE is that it provides an extra layer of security by encrypting our data from the moment it leaves our device until it reaches the intended recipient. Unlike traditional encryption methods, which often store our data on servers that can be vulnerable to hacking, E2EE ensures that even if a breach occurs, our information remains unreadable and useless to any unauthorized party.
No Access to Private Conversations or Data
Furthermore, E2EE guarantees that not even the service providers themselves can access our private conversations or data. This is a fundamental aspect of protecting our privacy against large corporations or government surveillance. By shifting the control of encryption keys to the end-users, E2EE removes the reliance on intermediaries and minimizes the risk of data breaches caused by third-party vulnerabilities or malicious actors within these organizations.
Promotes Trust and Transparency
Lastly, E2EE promotes trust and transparency between users. When we know that our communications are protected by strong encryption, we can freely express ourselves without fearing interception or monitoring. This is especially crucial for individuals or organizations dealing with sensitive and confidential information, such as journalists, activists, or businesses concerned about safeguarding trade secrets.
End-to-End Encryption Implementing

Implementing E2EE in your digital communications is now easier than ever. Numerous messaging apps and email providers offer this feature out of the box, allowing you to seamlessly encrypt your conversations. By opting for these services, you can ensure that your sensitive information, such as financial details or personal conversations, remains private and secure.
While E2EE provides robust security for your digital communications, it’s important to note that it does have limitations. It only protects the content of your messages and does not shield the metadata, such as the sender, recipient, or timestamp. Additionally, enabling E2EE may impact the usability of certain features, such as syncing messages across devices or searching through encrypted conversations.
Top Tools and Apps
Signal is a communication app that offers robust E2EE functionality for text messages, voice calls, and video chats. It has gained popularity for its strong encryption protocols and user-friendly interface. Another great option is ProtonMail, an encrypted email service that allows you to send and receive secure messages. With its end-to-end encryption, your emails are protected from prying eyes, even from the service provider itself.
For file storage and sharing, Sync.com is a top choice. It offers E2EE for your files, ensuring that only you and those you authorize can access them. With collaboration features and version control, it’s an ideal option for businesses and individuals alike. If you’re looking for a comprehensive suite of E2EE tools, VeraCrypt is worth considering. It provides disk encryption capabilities, allowing you to secure your entire hard drive, external storage devices, or even individual files and folders.
End-to-End Encryption on Samsung
Samsung integrates encryption in several ways, including:
- Secure Folder: Samsung’s Secure Folder leverages the defense-grade Samsung Knox security platform to create an encrypted space on your device. Here, you can store photos, videos, documents, apps, and data that you want to keep private.
- Samsung Messages and Email: For communication, Samsung Messages and Email apps support E2EE, ensuring that your conversations remain confidential.
- Samsung Knox: At the heart of Samsung’s security features is Knox, a multi-layered platform built into the hardware and software of most Samsung devices. Knox provides real-time monitoring and protection against malware and phishing attacks, and it includes E2EE to safeguard your data.
End-to-End Encryption on Email
For users of other email services like Gmail or Outlook, third-party encryption tools and plugins can provide end-to-end encryption capabilities.
Benefits of Using End-to-End Encryption for Email
- Privacy Assurance: Encryption ensures that only you and your recipient can read the content of your emails.
- Protection Against Cyber Threats: Reduces the risk of data breaches and cyber attacks.
- Data Integrity: Prevents unauthorized alterations to your email while in transit.
- Regulatory Compliance: Meets legal and regulatory requirements for data protection and privacy.
- Trust Building: Enhances trust between communicators by securing correspondence.
Common Misconceptions
One common misconception is that E2EE is only necessary for those engaging in illegal activities. This couldn’t be further from the truth. E2EE is essential for everyone, regardless of their online activities. It ensures that our personal and sensitive information, such as financial details and confidential conversations, remains private and inaccessible to unauthorized individuals.
Another misconception is that E2EE hampers law enforcement investigations by providing a secure communication channel for criminals. While it is true that E2EE makes it challenging for law enforcement to intercept and access communication content, this does not mean it hinders all investigations. It simply emphasizes the need for law enforcement agencies to adapt their investigation techniques to meet the evolving challenges of technology.
Lastly, some people believe that E2EE is only necessary when using certain applications or platforms. The reality is that E2EE can be implemented across various communication platforms, including messaging apps, email services, and even video conferencing tools. It’s crucial to prioritize platforms that prioritize end-to-end encryption to ensure a higher level of security for your online interactions.
End-to-End Encryption (E2EE) vs. Other Encryption Methods: A Comparison
E2EE is a method that ensures that only the sender and intended recipient can access the encrypted data, making it virtually impenetrable to any eavesdroppers, including service providers and governments. Unlike other encryption methods, which may involve a third-party intermediary or rely on trust in the service provider, E2EE guarantees the utmost privacy and security by eliminating any potential weak points in the communication process.
Compared to other encryption methods like symmetric or public-key encryption, E2EE offers an additional layer of protection. With symmetric encryption, a single key is used by both the sender and the recipient, which could be compromised if exposed. Public-key encryption, on the other hand, relies on a key pair – a public key to encrypt the data and a private key to decrypt it. However, in both cases, the security of the encryption depends on the strength and secrecy of these keys, which can be vulnerable to attacks.
Ensuring Compliance and Security

What sets E2EE apart is the fact that the encryption keys are generated and managed by the end-users themselves, rather than being stored on servers or controlled by third-party entities. This gives individuals and businesses full control over their data, minimizing the risk of unauthorized access or interception. By adopting E2EE, you can guarantee the privacy of your sensitive information, reducing the potential for data breaches and complying with privacy regulations.
Furthermore, E2EE provides an additional layer of protection for confidential information, including messages, files, and even video calls. This encryption method renders data unreadable by anyone other than the intended recipient, even if intercepted during transmission. This level of security is particularly crucial for industries dealing with sensitive client information, such as healthcare, finance, and legal sectors.
The Future of End-to-End Encryption in Data Security
End-to-End Encryption (E2EE) ensures that data is securely transmitted and received by only the intended parties, preventing unauthorized access or interception at any point along the way. This method encrypts the information on the sender’s device and can only be decrypted by the receiver, using unique keys that are not stored on any server. As a result, even if a hacker manages to access the data during transmission, they would be unable to decipher it without these keys.
The future of End-to-End Encryption (E2EE) in data security seems promising. Its effectiveness in safeguarding privacy has garnered support from privacy activists, tech-savvy individuals, and even major technology companies. E2EE has become a standard feature in popular messaging applications, allowing users to securely communicate and share important information without fear of interception.
However, despite its advantages, E2EE also faces challenges. Governments and law enforcement agencies argue that the enhanced privacy provided by E2EE may hinder their ability to monitor and prevent criminal activities. This has led to debates over balancing privacy rights with public safety concerns, raising the question of whether backdoors or alternatives to E2EE should be implemented.
Ultimately, the future of End-to-End Encryption (E2EE) in data security will depend on striking the right balance between privacy and security. As technology advances and cyber threats continue to evolve, it is crucial to find innovative solutions that protect sensitive information without compromising an individual’s right to privacy. Only through ongoing dialogue and collaboration between stakeholders can we ensure the long-term viability and effectiveness of E2EE in maintaining data security in an increasingly interconnected world.
Best Practices for Encryption Effectiveness

To maximize the effectiveness of E2EE, there are a few best practices to keep in mind. Firstly, it is crucial to use a trusted and reputable messaging or communication platform that offers E2EE. Not all apps or services provide this level of encryption, so it is essential to do your research and choose one that prioritizes security.
Secondly, always keep your apps and devices up to date. Software updates often include bug fixes and security patches that can enhance the effectiveness of E2EE. By staying current with these updates, you ensure that any vulnerabilities are addressed, reducing the risk of data breaches.
Another important aspect is to carefully manage your encryption keys. End-to-End Encryption relies on strong encryption keys that only the sender and recipient have access to. It is crucial to protect these keys and avoid sharing them with anyone else. Additionally, regular key rotation is highly recommended to further enhance security.
Lastly, it is important to continuously educate yourself on the latest security practices and stay informed about potential threats to E2EE. Technology is constantly evolving, and staying ahead of the curve is crucial in protecting your sensitive information.
By utilizing E2EE, individuals and businesses can have peace of mind knowing that their private conversations, confidential documents, and sensitive information are protected. Whether you are sending an email, chatting on a messaging app, or conducting online banking transactions, E2EE ensures that your data remains secure from prying eyes.
However, it is important to note that E2EE is not a foolproof solution. While it greatly reduces the risk of unauthorized access, it does not guarantee complete privacy. There are still potential vulnerabilities, such as malware or keyloggers, that can compromise the security of your data. It is essential to stay vigilant, keep your devices updated with an antivirus protection, and use strong passwords to further enhance your online privacy.
Safeguarding Your Privacy Online

In an age where our lives are increasingly intertwined with technology, safeguarding our privacy online has become more important than ever. One powerful tool that can help protect our digital information is End-to-End Encryption (E2EE). By securing data at all stages, E2EE ensures that only the intended recipients can access the information, making it virtually impossible for third parties to intercept or decode sensitive data.
Unlike other encryption methods, E2EE encrypts data on the sender’s device and decrypts it only on the recipient’s device. This means that even if the data is intercepted during transmission, it remains indecipherable to anyone without the proper encryption keys. In other words, E2EE provides the highest level of privacy and security when it comes to online communication and data sharing.
Conclusion
The importance of E2EE cannot be overstated in today’s digital landscape. With the growing prevalence of cyberattacks and data breaches, individuals and organizations need to adopt robust security measures to protect themselves against potential threats. By utilizing E2EE, you can have peace of mind knowing that your personal information, financial details, and sensitive conversations are safe from prying eyes.
In conclusion, safeguarding your privacy online should be a top priority in today’s interconnected world. End-to-End Encryption (E2EE) offers a reliable and effective solution to protect your digital information from unauthorized access. By implementing E2EE, you’ll be taking a proactive step towards preserving your privacy and ensuring that your online activities remain secure. So, whether you’re sending private messages, conducting business transactions, or simply browsing the web, remember to prioritize E2EE and keep your personal information safe.
FAQs on End-to-End Encryption
What is end-to-end encryption (E2EE)?
End-to-end encryption is a method of secure communication that prevents third-parties from accessing data while it’s transferred from one end system or device to another. It ensures that only the sender and the intended recipient can read the message content.
How does end-to-end encryption work?
E2EE works by encrypting the data (such as messages or files) on the sender’s device and keeping it encrypted while it travels across the internet, only to be decrypted on the recipient’s device. This process utilizes cryptographic keys unique to each user.
Why is end-to-end encryption important?
E2EE is crucial for privacy and security online. It protects sensitive information from being intercepted by hackers, government agencies, and even the service providers themselves, ensuring that only the communicating users can access the content.
Can end-to-end encrypted data be intercepted?
While the encrypted data can technically be intercepted during transmission, it remains indecipherable without the unique decryption key held only by the recipient, making the information useless to interceptors.
Does end-to-end encryption protect against all forms of surveillance and hacking?
E2EE significantly increases security and privacy by encrypting content. However, it doesn’t protect against endpoint security threats (such as malware or spyware on the sender or recipient’s device) or metadata analysis.
Which applications use end-to-end encryption?
Many messaging apps and email services use E2EE to protect user data. Prominent examples include WhatsApp, Signal, ProtonMail, and Tutanota.
How can I tell if an app uses end-to-end encryption?
Look for statements in the app’s security settings or their official website/documentation. Many apps proudly advertise their use of E2EE as a key privacy feature.
Can I enable end-to-end encryption on services that don’t offer it by default?
For services that don’t offer E2EE by default, you may be able to use third-party encryption tools or plugins to secure your communications. However, this depends on the compatibility of the service with such tools.